Form Spoofing
by Rekha[ Edit ] 2009-11-13 12:40:36
Here is the best form spoofing example.
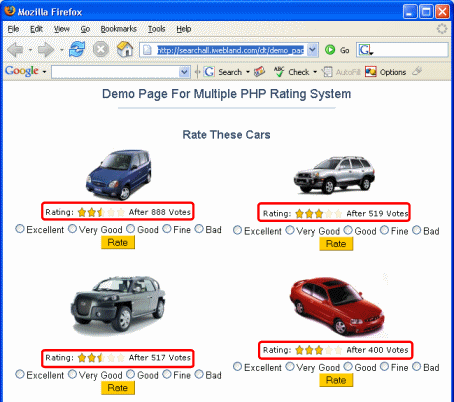
Here is the html code for a car-rating form before modification:
<form method=post>
Rating: <img src="./25star.gif" alt="Average rating: 2.9361702127662"> After 517 Votes
<input type=radio name=note value=5>Excellent
<input type=radio name=note value=4>Very Good
<input type=radio name=note value=3>Good
<input type=radio name=note value=2>Fine
<input type=radio name=note value=1>Bad
<input type=hidden name=envoi value=1>
<input type=hidden name=mpo value=2>
<input type=submit value=Rate>
</form>
First, take a look at the form tag. There is no action attribute. It means that the form will be submitted to the same URL. The user copy the URL from the browser and added an action attribute to the form tag.
Second, look at the rating average. He want to make it greater than 5 to get my five stars. So, He modified the value of the first input tag from 5 to 5000. Now, the "excellent" choice has a value of 5000.
Here is the result
<form method=post action="http://searchall.iwebland.com/dt/demo_page.php">
Rating: <img src="./25star.gif" alt="Average rating: 2.9361702127662"> After 517 Votes
<input type=radio name=note value=5000>Excellent
<input type=radio name=note value=4>Very Good
<input type=radio name=note value=3>Good
<input type=radio name=note value=2>Fine
<input type=radio name=note value=1>Bad
<input type=hidden name=envoi value=1>
<input type=hidden name=mpo value=2>
<input type=submit value=Rate>
</form>
For each car, the user chose the "excellent" radio button and clicked "Rate".
Here is the result:
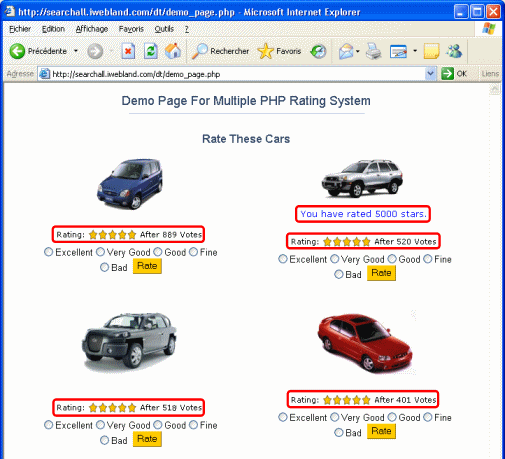
All cars get 5 stars with one click. Look at the number of votes (+1).
Conclusion:
In this example the guy assumes that the value of the chosen option is between 1 and 5 and has never thought that it can be modified by a user.
NEVER, NEVER trust the user input data. Filter all what you get from the user: forms, cookies, request headers, etc...

